Today, loopholes have become a serious threat in the IT field. From time to time, security vulnerabilities that are exposed from time to time, coupled with the influx of certain media, have caused users to be at a loss or panic. In fact, any IT system has the potential for loopholes. So how do we think about and how to deal with these loopholes? Where is the vulnerability of the loopholes and how should we guard against it?
A few months ago, OpenSSL's "bleeding heart" blew up. This loophole seems to be a sudden discovery that everyone is using a latched-in security problem that can be easily exploited by an attacker. If all the locks in the world are in name only, they do not know how much panic it will cause.
In the early morning of August 7, Beijing time, the famous “2014 Black Hat Conference†was held in Las Vegas, USA. At the meeting, there were many security holes exposed: For example, a USB vulnerability could allow attackers to modify the USB host firmware to convert various USB devices (not only U-disks but devices with USB interfaces) to Attack Tools; Qualcomm Snapdragon Processor Vulnerabilities May Lead to the Risk of Information Disclosure for Almost All Cell Phones Using the Processor; Certain Aircraft Communication Device Firmware Vulnerabilities May Cause Attackers to Use Wi-Fi Networks or Aircraft on Aircraft In-flight entertainment information systems invade aircraft avionics, interrupt or modify satellite communications, interfere with aircraft navigation and security systems...
The emergence of these loopholes is even more appalling. In the face of these endless loopholes, we cannot help but ask: How do we view these security loopholes? For safety, is it not the best choice to abandon all electronic equipment and systems back to the "primitive society"?
In fact, the vulnerability is likely to exist in any IT system. Human beings are not perfect. The IT systems created by humans are also not perfect, but it is clear that we have long been inseparable from these "imperfect" systems. These "imperfect" systems have pushed human society forward. We should not talk about the change of loopholes, but we should calmly observe and understand the causes of the security loopholes to find a solution to the loopholes before they can make a change.
Balance is broken
Some of the security breaches seem to be far away from us, but they are actually very close to us. Many people may not know that on the desktop operating system that we use every day, there is always an offensive and defensive battle against system vulnerabilities.
Four months ago, the Microsoft Windows XP outage service incident caused a great uproar in the field of domestic information security. After all, the Windows XP out of service event is a typical case of vulnerability protection. As we all know, Microsoft regularly publishes patches to patch its software, especially the flaws and functional flaws in the operating system. Windows XP stopped its service, that is, Microsoft announced the termination of the operating system Windows XP has been in service for more than a decade to patch, no longer released on Windows XP patch.
Zhang Cong, a senior security researcher at Qihoo 360, told the China Computer News that due to the widespread use of Microsoft's Windows operating system on the PC side, there are some black interest chains all over the world. They are constantly digging through security holes on Windows systems and then using them. These security vulnerabilities attack users and gain illegal benefits. On the other hand, many security vendors and white hats are also exploiting security vulnerabilities on Windows systems. They are immediately reported to Microsoft for repairs by Microsoft. This is also the origin of Microsoft security patches. .
"Always, the black interest chain has been dynamically balancing the exploitation and utilization of Windows XP security vulnerabilities with Microsoft's repair of security vulnerabilities. However, Microsoft's service incident to stop Windows XP has broken the security vulnerabilities in Windows XP. The balance, that is, because there are still a large number of users using Windows XP, the black interest chain will not stop the exploitation and exploitation of Windows XP security vulnerabilities, and on the other side, Microsoft has stopped patching the security vulnerabilities of Windows XP. This makes the threats faced by users of Windows XP amplify, and it is even more important to prevent the security threats of Windows XP.†Zhang Cong said.
Win by winning
In fact, the "zero-day attack" is also one of the words that can often be heard in the field of information security in recent years. Many security vendors believe that the prevention of zero-day attacks is the focus and difficulty of today's cyber attacks. The so-called zero-day attack is an attack initiated by an attacker using a zero-day vulnerability. The zero-day vulnerability does not refer to a specific security hole. Instead, it refers to an attacker who immediately exploits the vulnerability after discovering a security hole, attacks the user system before the vulnerability is repaired, and even before the vendor issues a patch for the vulnerability. The attack has already succeeded.
It can be seen that the response time is very important for the prevention of vulnerabilities. A zero-day attack using zero-day loopholes is the result of attackers using time differences to make quick attacks.
Beijing Security Source Li Peng told reporters that after the XP era users face a series of security issues. The first is the zero-day vulnerability that hackers may have accumulated. After Windows XP stops service, Windows XP will always suffer from zero-day vulnerability. According to official Microsoft data, Windows XP system users are six times more exposed to hacking than users of Windows 8 systems. The second is system flaws that pose security threats to personal privacy and corporate secrets. The third is the APT attack. The fourth is how to ensure the stable operation of important information systems on XP and how to ensure stable and rapid operation of the operating system. The last point is how to ensure the safe operation of a large number of information systems and application software.
"Beasen has long realized that the Windows XP outage incident will have a huge impact on the operating system security of our users. The speed at which we can take action to respond is also very fast." Li Peng told reporters that Beixinyuan was back in December last year. It was the first to release the "Ace line" that provides security protection for Windows XP, and placed several lines of defense on Windows XP. The first line of defense is the reinforcement of the system security baseline. Based on the Microsoft system security baseline, it comprehensively collects system vulnerability information and security issues. It conducts unified investigation of various security risk points to form a complete detection and management solution, helping managers predict security risks. , to gain insight into security risks and achieve unified configuration management of security policies. The second line of defense is the system fortress, through the process of black and white list management and signature filtering, malicious program identification and software behavior control, to achieve the safe loading and execution of the operating system process. The third line of defense is data security protection. It adopts a data lifecycle security model, combines user behavior depth analysis, security containers and other technologies to solve data security problems such as data generation, storage, distribution, and reading. In addition, the "Ace of Defense" also has data firewalls, active defenses and other defenses, data backup and recovery, sensitive information inspection methods, and has a strong patch support system.
Based on nearly 20 years of industry experience and tens of millions of end-users' application experience, Beixinyuan has formed a comprehensive patch support system and vulnerability defense system to quickly identify and actively prevent potential operating system vulnerabilities. The entire network immediately issued patches, reducing The risk of malicious attacks and data leaks caused by system vulnerabilities to users.†Li Peng said, “A line of defense†provides functions such as patch verification, distribution, installation, recycling, rollback, and some other aspects of system security. Protection functions, such as health check and optimization of the system, trace crushing, data safes, outsourcing of file authorizations, security management of removable media, etc.
"Even if the system is not patched, the "Ace line" can withstand more than 90% of malicious attacks. In terms of enterprise terminal system management, it can also reduce the company's management costs and the workload of system administrators. It is particularly suitable to help companies in various industries to overcome the operating system transition period of Windows XP, said Li Peng.
New ideas for defense
It is undeniable that attackers use vulnerabilities to attack, which puts a greater challenge on security protection than viruses and Trojans. Zhang Cong told the reporter: “In the past, especially in the era when security software and security technology were not widely used, attackers could achieve the effect by writing viruses and Trojan horse programs to achieve an effect and make their evil purpose successful. However, with the Internet, With the popularity of security software, it is difficult for attackers to commit evils through viruses and Trojans. This forces them to focus their attention on the higher security loopholes in technology."
Indeed, although the loopholes have existed, more attacks have come from exploiting security vulnerabilities, which is also a trend that has emerged in recent years. Although exploiting vulnerabilities to increase the attacker's technical threshold, security protection software is more difficult to protect.
"Previously, technologies for the protection of viruses and trojans were based on feature libraries for identification and disposal. However, in the era of vulnerability, protection has not been possible based on feature libraries." Zhang Cong told reporters that the use of viruses, Trojans to attack A significant difference from exploiting an exploit is that it requires an entity to exploit viruses and Trojans. It is relatively easy for the protection software to identify the virus and Trojan's entity and dispose of it. Exploit attacks are often just a piece of script, security software. It is difficult to find the abnormal condition of the system and it is difficult to identify the attack and capture the sample.
"The loopholes are limitless, but the use of the loopholes is limited." Li Peng thinks. In the face of exploiting this new type of attack, there must be new ideas for protection.
Zhang Cong told reporters that in the face of the security risks caused by the suspension of Windows XP service, in the absence of official patches, different and previous solutions must be adopted. It is understood that Qihoo 360's security protection tool “XP shield armored†adopts the three core security policies of hot patching, reinforcement, and isolation to implement protection for Windows XP. "The most direct and effective way to deal with the security threats posed by exploitation of vulnerabilities is to apply patches. However, if a vulnerabilities arise, this is not the official system for Windows XP, which is not officially provided by Microsoft, or the official version of Windows 7 or Windows 8. The situation that the patch has not yet been released is difficult for the user to get corresponding protection at the first time.360 provides the user with a hot fix (Hotfix) as an alternative solution.To date, 360 has been a zero-day vulnerability for Microsoft operating systems. Twenty-two hot patches were provided to cover all the high-risk vulnerabilities that broke out in the past six years. Zhang Cong told reporters that hot patches can be found immediately and solved immediately. 360's patching engine serves as a quick response mechanism and can modify the operating system without modification. Under the premise of the file, after the system is running, the vulnerability is quickly repaired, quickly deployed, and applied.
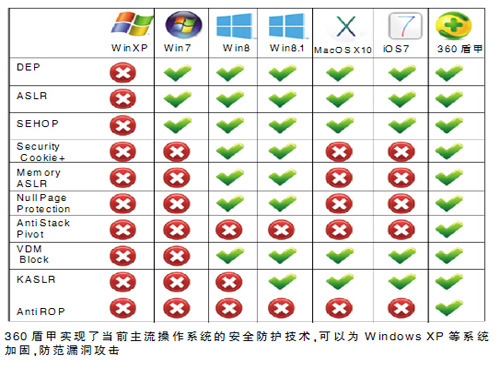
In fact, because Windows XP was born earlier, it was limited to the level of software and hardware at that time. Compared with current operating systems, it lacked many key security protection technologies, such as DEP data execution protection, ASLR address randomization, and SEHOP. According to reports, 360's "XP shield armored" uses these technologies to achieve the reinforcement of the user operating system. "To be prepared in advance, we must not only address specific vulnerabilities, but must also strengthen the kernel of the operating system, strengthen kernel security, and prevent system kernel loopholes." Zhang Cong said that "XP Shield A" is missing for Windows XP. Limitations on code execution permissions, lack of kernel-level randomization of memory, lack of protection for 0 pages of memory, lack of protection against structured exception handling chains, and other weaknesses were actively reinforced. In addition, "Xp shield" also provides additional protection for the Windows XP kernel, such as disabling dangerous kernel calls, additional checks before entering the kernel, and so on.
"Even if an attack exploiting a vulnerability is smart enough to bypass 360's thermal patching and hardening techniques, it may still not succeed because we have isolated sandbox technology." Zhang Cong told reporters that when sensitive programs are running, Will be isolated in the sandbox, "XP shield A" sandbox will have many restrictions on the program, such as limiting access to sensitive data on the operating system, etc., in order to achieve the protection of the system. Sandboxes are introduced in iOS, Google Chrome, and other software. This allows attackers to perform dangerous operations even through webpage or document exploits. These operations are also trapped in the sandbox and cannot cause further damage to the system.
"However, implementing full sandbox protection on Windows XP is not easy. This is because sandbox technology requires a lot of underlying system support. However, many security mechanisms for the Windows platform are added after the Vista version. Windows XP can support it. The security mechanism is limited." Zhang Cong said, "To implement a complete sandbox protection on Windows XP needs to complete the 'foundation' on the operating system first, which is more difficult than sandbox protection on Windows 7 and Windows 8. More often than not, it also tests the technical strength of a security vendor."
From the hot patch to the reinforcement to the sandbox, Qihoo 360's idea of ​​Windows platform vulnerability protection is very clear, from the patch protection against vulnerabilities, to the overall reinforcement of the operating system, and then to the use of sandbox isolation, such protection ideas It is completely different from the previous proactive detection, active identification, and blocking. The protection idea of ​​this set of Windows platform vulnerabilities can in fact be borrowed from the vulnerability protection of other software systems.
Vulnerability to be open and transparent
As vulnerabilities become more and more popular methods of attack, the scramble for exploiting and repairing vulnerabilities is far from stopping. In fact, in terms of vulnerability attacks and defenses, it is the attackers and defenders who can exploit the loopholes first. It is the attackers who first exploited the loopholes and implemented attacks, or whether the defenders took the lead in duplicating loopholes and repairing the loopholes.
To protect the vulnerability of Windows platforms, especially Windows XP, it is imperative to monitor the vulnerability and respond quickly. Zhang Cong told reporters that Qihoo 360, as a partner of the Microsoft MPP (Microsoft Active Protections Program) program, closely exchanged vulnerability attack and protection information with Microsoft to provide timely protection for users. At the same time, Qihoo 360 will also learn about newly discovered vulnerabilities through some public methods, and discover some vulnerabilities by itself, or study Microsoft's announcement of Windows 7 and Windows 8 vulnerabilities and test whether it exists on Windows XP systems.
It is because of loopholes in the offensive and defensive battles that the exploitation and discovery of vulnerabilities is very important, so the role of the vulnerabilities platform is gradually highlighted because it can form a benign information transmission between the vulneraventors (usually white hats) and vulnerabilities manufacturers. At the same time provide the public with warnings. With the growth of the use of loopholes, the third-party vulnerability platform has also gradually grown to become a force that can not be ignored in defending the vulnerability. For example, the cloud vulnerabilities platform (WooYun.org) has grown up in recent years.
Wuyun Vulnerability Platform was established in 2010. It is currently a large-scale security vulnerability warning platform and network security community in China. It is active in nearly 10,000 white hats and can pass vulnerability information to all industry customers at the first time (government, finance, Operators, state-owned enterprises, and mainstream internet and technology companies. Yun Di, director of platform marketing for the cloud vulnerabilities, told reporters that so far, the vulnerabilities received by the vulnerabilities platform platform have received nearly 100,000 vulnerabilities and received an average of 100 or more per day. There are more than 1,000 white hats registered on the platform and more than 500 registered companies. The vulnerability information of users in various industries is transmitted through cooperation with the National Internet Emergency Response Center.
Yu Di told reporters that Wu Yun formulated a set of reasonable loopholes and approval mechanisms to fully mobilize the enthusiasm of white hats and enterprises. This set of mechanisms not only allows White Hat to actively submit details of loopholes to companies, help companies assess the severity of vulnerabilities, but also enable them to solve vulnerabilities at the earliest opportunity and avoid users from suffering losses.
"The significance of the third-party vulnerability platform is also to enhance our country's overall information security awareness and level." Yu Di told reporters, "In the early days, some companies have conflicted with this platform and believe that the practice of open loopholes in the platform is to discredit companies. However, after they learned about the platform, they began to actively face and solve security problems.Now, many companies that have not been disclosed have voluntarily registered in the cloud, hoping to have white hats to disclose their loopholes and help them improve.â€
"On the vulnerabilities platform like dark clouds, white hats can continue to learn and grow. Enterprises can discover their own problems and risks in a timely manner and learn from other vulnerabilities on the platform. The general public can clear up misunderstandings about Internet security. Improve personal safety awareness, and at the same time be more confident in personal privacy, data, and property security,†said Judi.
In fact, the dark cloud vulnerability platform has built a bridge between enterprises and white hats, so that various directional value-added services can be carried out. “We believe that the loopholes should be open and transparent, and openness can put pressure on companies and promote the timely repair of loopholes. At the same time, openness can raise public awareness of safety and enhance the status of white hats in the interaction between white hats and companies." Di told reporters, "Of course, there are strict and reasonable disclosure mechanisms for dark clouds. We don't blindly disclose them after discovering vulnerabilities. We will not allow these vulnerabilities to be used maliciously by attackers and cause social panic."
Judi believes that compared with other vulnerabilities platforms, Wuyun Vulnerability Alerting Platform can ensure the accuracy and openness of vulnerabilities, and has far more popularity and data than other platforms, making vulnerabilities in the cloud platform's vulnerabilities more accurate and capable of warnings. Reflect the real situation of China's Internet security.
Look at the loopholes as "birds"
Some people say that when an ostrich is in danger, he will bury his head in the haystack, thinking that his own eyes cannot see the danger and he will be safe. Psychologists also refer to the negative attitude people face when they are threatened as the "ostrich mentality."
Vulnerabilities may have a long latency, which means that even if a vulnerability is exploited and completed by an attacker, if the user does not find the vulnerability and fix it for a long time, the "door" has been in the user's On the system, it is open to other attackers and users may not know it. However, the loopholes are “invisible and intangible†and have a strong concealment, which just makes some companies have an ostrich mentality.
“The role of the vendor is actually the most critical aspect of the protection against vulnerability attacks. If manufacturers always have a flirtatious attitude, or are reluctant to face the danger like an ostrich, and do not actively respond to and handle the loophole, it may cause a wide range of Security crisis, this approach is also not responsible for their own users." Zhang Cong said.
However, for ordinary users, besides upgrading software in a timely manner and patching vulnerabilities, it seems that there is no way to exploit vulnerabilities. Zhang Cong told reporters that even if it is a vulnerability attack, it also needs a carrier. It also requires the user to have a good sense of security and maintain a high degree of vigilance, such as not clicking on strange links or emails.
"The recent emergence of applications such as Internet of Vehicles, Internet finance, smart homes, and wearable devices has made the loopholes more and more widespread. As these emerging technologies and applications are just starting, companies are still learning about their security at an early stage, but Wuyun has taken note of these trends and guided Bai Hat to pay attention to the loopholes in these areas and provide targeted and valuable security alerts so that relevant companies can focus on the security issues in these areas.†Judy said that any system has loopholes. Possible. Although the current awareness of corporate security has risen significantly, but when these emerging technologies and applications have become a climate, the security awareness of related companies and the attitude toward the loopholes are also worth our attention.
Links to the Top 10 Security Vulnerabilities Announced by the Dark Cloud Vulnerability Platform
1. Internet leak incident/attack attack
Based on a large amount of user data, use the same registration habits (same username and password) as the user to try to log in to other websites. Since 2011, the Internet leakage incident has triggered the entire information security industry, leading to the traditional way of user name + password authentication can no longer meet the existing security needs. Case: CSDN database leaked, a large number of users real account password leaked.
2. Refer to unsafe third-party applications
Over the past few years, the security sector has made great strides in how to address vulnerabilities. Almost every business system increasingly uses third-party applications, which in turn increases the threat of system intrusion. As third-party applications are deployed in parallel on business systems, if a vulnerable third-party application is used, such attacks will result in serious data theft or system collapse. These third-party applications include open source applications, components, libraries, frameworks, and other software modules. Case: Inappropriate operation and maintenance of Taobao's main station can cause random users to log in and obtain server-sensitive information.
3. Systematic mistakes / logical defects caused by violence guess
Because the application system's own business features will open up many interfaces for processing data, if the interface or function is not subjected to rigorous security control or judgment, it will prompt the attacker to accelerate the process of attacking the application program and greatly reduce the cost of the attacker discovering the threat. With modularization and automated attack toolkits becoming more sophisticated, this will pose a great threat to applications. Case: Big company defect series #1 resets Jingdong arbitrary user password.
4. Leakage of sensitive information/configuration information
Because there is no common standard defense rule to protect middleware configuration information, DNS information, business data information, user information, source code backup files, version management tool information, system error information and sensitive address information (background or test address), etc. A person may use this information to perform further attacks on the system by collecting these under-protected data. Case: Ctrip's secure payment log can be traversed and downloaded, resulting in the disclosure of a large number of user bank card information (including the cardholder's name ID card, bank card number, card CVV code, and 6-digit card Bin).
5. Application misconfiguration/default configuration
Prior to deployment, application, middleware, and server-side programs do not have strict security configuration definitions and deployments for security baselines, which will facilitate attackers to implement further attacks. The common risks are: Flash default configuration, default address of Access database, WebDav configuration error, Rsync error configuration, application server, Web server, default background and management password of database server's own management function. Case: Sensitive Information Disclosure Series #6 The default configuration of the server resulted in massive user information leakage.
6. SQL injection vulnerability
Injecting defects is not limited to SQL. It also includes commands, code, variables, HTTP response headers, and XML injections. The programmer does not determine the legitimacy of the user's input data when writing the code. Injection occurs when untrusted data is sent to the interpreter as part of a command or query. The attacker's malicious data spoofing interpreter allows it to execute unexpected commands or to access data without accurate authorization. Case: SQL injection vulnerabilities of Shrimp.com, with 14 million user data and various transaction data and master station data can be dragged and dropped.
7. XSS Cross-Site Scripting/CSRF
It is a kind of code injection. XSS occurs when the application gets untrusted data and sends it to the browser or supports the client-side scripting language container without proper validation or escaping. XSS allows an attacker to execute a script line on the victim's browser, thereby hijacking a user's session, destroying the site's Dom structure, or redirecting the victim to a malicious website. Case: A vulnerability that can steal Taobao/Alipay accounts and passwords silently (buried thunder attacks).
8. Unauthorized access/authorization bypass
Most business system applications only check the authorization information on the user client, or simply do not limit access control rules. If the server does not check the integrity of the request from the client, the attacker will be able to forge requests and the access is unauthorized. The function used. Case: An important backend of Sogou has not been granted access (involving important functions and statistical information).
9. Strict control of the account system/override operations
Application functions related to authentication and session management are often exploited by attackers. Attackers can retrieve user passwords through a social engineering database that has been organized, or obtain information such as secret keys, session tokens, GSIDs, and other information to bypass authorization. Control access to data that is not your own. If the server does not check the identity of the request from the client, the attacker can use the forgery request to steal data of all service systems. Case: LeTV's 22 million users have excess risk.
10. Internal data/document leakage
Both companies and individuals increasingly rely on the ability to store, process and transmit information to electronic devices. The important data information of the enterprise is stored in electronic devices or data centers in the form of documents. For the convenience of the office, the employees or programmers of the company often copy the confidential data to a removable storage medium or upload it to the network. Once the information is leaked, it will be Increase the probability of corporate security risks. Case: Taobao sensitive information leakage can enter an important background (using a lot of sensitive features and control internal servers).
Commercial Lighting Led Driver
With Commercial lighting tend to be led lighting mode more and more, Led Lighting Solutions became the most verriding concern issue at the lighting area. We have skilled engineers to answer all your questions and enquiries and provide all-round solutions basis on your project(s) and provide technical supporting. Energy saving and environmental protection are always Fahold's aim, Specializing in LED lighting drivers design, Products apply to street light, industrial and mini light, linear light, tri-proof light, flood light, panel light and so on.
Parameter:
Input voltage: 100-277vac / 100-240vac / 100-130vac / 180-240vac / 100-347V
output voltage: 25-40vdc / 27-42vdc / 35-45vdc / 50-70vdc / 12Vdc / 24vdc
current: 100mA-8000mA.
Power factor: >0.95
Dimming: 0-10V / PWM / RX / DALI/Traic dimmable
>=50000hours, 3-5 years warranty.
certificate: UL CE FCC TUV SAA ect.

FAQ:
Question 1:Are you a factory or a trading company?
Answer: We are a factory.
Question 2: Payment term?
Answer: 30% TT deposit + 70% TT before shipment,50% TT deposit + 50% LC balance, Flexible payment
can be negotiated.
Question 3: What's the main business of Fahold?
Answer: Fahold focused on LED controllers and dimmers from 2010. We have 28 engineers who dedicated themselves to researching and developing LED controlling and dimming system.
Question 4: What Fahold will do if we have problems after receiving your products?
Answer: Our products have been strictly inspected before shipping. Once you receive the products you are not satisfied, please feel free to contact us in time, we will do our best to solve any of your problems with our good after-sale service.
Commercial Lighting Led Driver
Commercial Lighting Led Driver,Constant Led Driver Circuit,Led Lighting Solutions ,Led Driver Power
ShenZhen Fahold Electronic Limited , https://www.fahold.com